Lots of people claim to have “the secret” to promoting books. After all, your book is awesome, isn’t it? The problem must be that you aren’t promoting it. You can attend workshops, courses, and buy books that all proclaim The Secret.
For SSH Mastery, I’m responsible for all of the promotion. I’ve followed the usual advice: I have a blog, I have Twitter, I have a fan page on Facebook, and so on. You can stalk me through any method you choose. I also have real-time access to sales data from Amazon, Smashwords, and Barnes & Noble.
For this example I’m going to use Amazon data, because Amazon provides very nice graphs through Author Central. If you’re an author and you are not on Author Central, get on it NOW. (Then check it only once a month or so.)
Here’s the graph for Kindle sales of SSH Mastery, since its release.
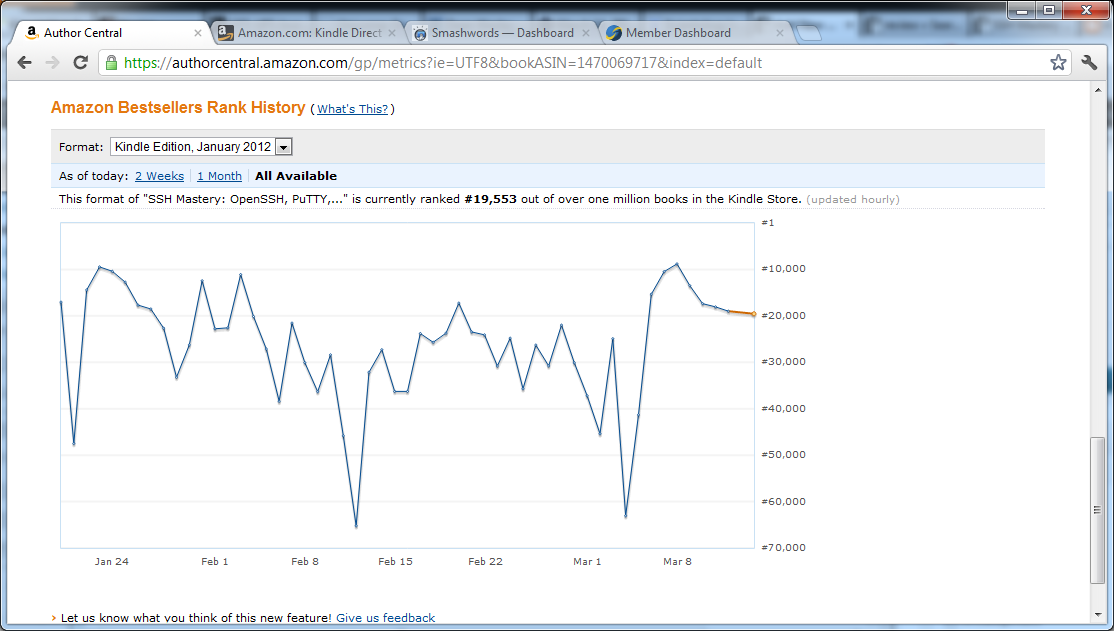
Note that Amazon’s sales ranking algorithms are rather mushy. More than once, according to Author Central, this book has cracked the #10,000 limit. Most of the time, Amazon retroactively changes that. The peaks shown are generally within a day or two of when the sale took place, however. While this is undesirable, it’s better detail than the quarterly or biannual resolution you get from a publisher.
So, what have I done to promote SSH Mastery? I’ve blogged it. I blog every time it gets a mention in the press. The blog goes into Twitter and Facebook. I also comment on the book via Twitter.
I also thank people when they say they buy the book or when they review. Even when they don’t like the book. (This book has received all five-star reviews, but more on that later.) Being known as a nice guy, or at least a polite one, or at least “not a screaming jackass,” has publicity value all its own.
So, how does all this impact book sales?
There’s been four reviews or “general public statements about the book that might not be exactly a review” that I know of:
Peter Hansteen, 22 Jan 2012
Justin Sherrill, 2 Feb 2012
Alexander Leidinger, 3 Feb 2012
Richard Bejtlich, 6 Mar 2012
(Wow. I forgot to blog Bejtlich’s review. He is my biggest fan and a staunch advocate of my work, and I completely failed to blog his review. I done him wrong. I’m a doofus.)
There’s also been good reviews posted on all of the ebook sites. I don’t appreciate them any less, but those reviews only help when people go to the retailer’s site. That means that they already know the book exists.
Compare those dates to the spikes on the graph. Keep in mind the mushiness of the Amazon ranking algorithm. You’ll see that the spikes roughly match up with the reviews. (If I had taken snapshots of this graph on the actual day and the day after the review, the spikes would be much more apparent, but I didn’t think of that until today. Yep, I’m a doofus.)
There’s another small spike around 20 February that I have no explanation for. I don’t know why it’s there, but I’m glad to see it.
The initial high sales came from the folks who follow me via my blog, Facebook, Twitter, or some other promotional medium. I was thrilled to see fans buying my work, and of course I appreciate every sale. But that surge didn’t last long, and it’s not enough to sustain a career.
But reviews expose the book to entirely new audiences. Reviewers are force multipliers. Nurture them.
In my case, the reviews are all positive. If I really wanted to do an experiment to test the “reviews are the only effective publicity” hypothesis, I’d write a lousy book and see how those reviews impacted sales. But my authorial pride outweighs my scientific curiosity.
So, the most effective promotion tool? Reviews.
Other than that: Shut up and write. No, quit jabbering and babbling. Shut up and write. Those words you’re going to use on a comment on this blog post? Put that energy into making your book awesome.
Shut up and write.