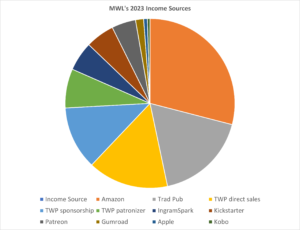
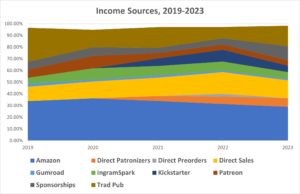
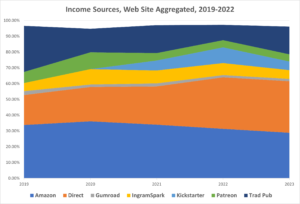
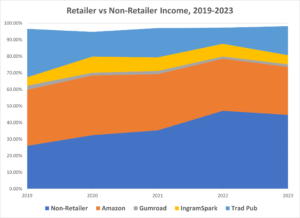
This post went to Patronizers at the beginning of November, and the public in December. A buck a month gets you early access and more.
These posts need titles, so I go for alliteration. Alliteration gives me an excuse to grab my primordial Oxford English Dictionary. I’ve mentioned this before, but I don’t think folks quite appreciate what a font of wordage it is.

It’s ninety years old and smells like knowledge.
Anyway, it’s been quite a month. The Apocalypse Moi Kickstarter is now completely fulfilled. Just as I was writing this sentence, though, the doorbell rang. UPS dropped off two packages, and—yep. It’s two copies of the book, dropshipped from the printer. They were supposed to go to backers. Instead, they went to me. Did I screw up entering the address? Possible. Did the printer screw up? Very possible. Did the printer’s obtuse web-based ordering system refresh inconveniently and overwrite my meticulously hand-entered shipping address with the default address? Screechingly possible. Each has a shipping slip with an order number, so I get to go through the orders and figure out who got shorted.
Or maybe the printer got carried away and shipped me extra books. That happens, too.
If it wasn’t for the lack of conference calls, I’d call this the worst business ever. But then I’d remember working in the auto industry and realize it’s not nearly that bad.
Anyway. That Kickstarter’s over except for the lingering cruft.
I’m to the bit of Run Your Own Mail Server where I get to talk about filtering and greylisting and SPF and all those fun topics. That’s not a huge topic, but it might take me a little longer than I’d like to get through. Which is the story of this book. October was a crunch month for my family. The crunch ends next Monday and I’ll be free to spew words. I’m learning things about email that I didn’t want to know, and details about workarounds that I didn’t want to know. Here’s yesterday.
Postfix’s postscreen(8) performs sanity checks on incoming email connections. Spambots behave badly, taking full advantage of Jon Postel’s original Robustness Principle. Postscreen identifies those bad actors and prevents them from talking to the SMTP server. Seems fine, right?
Postscreen has optional checks that are intrusive. It does most of the SMTP transaction and, if the client behaves well throughout, adds the client’s address to a temporary allowlist. The problem is, it can’t forward that connection to the mail handler. Instead, it gives the client a 400 error to say “I’m sorry, I can’t finish this right now, please come back later.” That’s a normal part of the email protocol. When the client returns, postscreen sees the address on the allowlist and steers it straight to the SMTP server. Simple enough.
Some of you might recognize that as greylisting. Greylisting is a controversial topic that I’m not gonna get into right now, but it is what it is. How does one get email delivered immediately, while still performing sanity checks? In theory, when a mail client can’t deliver to the primary mail server, it should immediately try the backup. Small sites don’t need a backup mail server.
But you can make a faux backup server.
Add a second IP address to your mail server. List it as the backup MX.
The client goes to the primary MX, passes the intrusive tests, and gets the 400 error. It immediately goes to the second MX. That’s the same host, so it has the same temporary allowlist. The mail is immediately accepted. You need to set up the backup MX address so that SMTP connections that arrive there cannot be added to the allowlist, but that’s included in Postfix.
So I go and set this up. I dig through Vultr’s web interface until I find how to get a second IP address and how to add it to a host. I add a second IPv6 address to that test host. Reboot everything, make sure all the connectivity works. Set up Postfix as a faux backup MX, adjust the DNS records. None of this is advanced work, but it’s tedious and annoying and type-prone. But at last everything looks correct, so I go to my other test host and send an email.
The test host tries the IPv4 address, and gets a 400. Good.
The test host tries the IPv6 address. 400. Good.
And then… it stops.
Postfix doesn’t try the backup MX. Why not?
I go to my old mail server, the one that’s running Sendmail. It gets a 400, immediately tries the backup MX, and sails through. Exactly the way it should. I’ll be trying with gmail today, see what they do. While gmail retries delay-queued mail from different IP addresses, I have no idea if the immediate retries change addresses. It’s an interesting test.
But I worked in IT for decades. I know perfectly well that if someone deployed this in the real world and something went wrong with an incoming message, a manager would ask “Are they on the list?” Because that’s what they ask. That meant I had to figure out how to interrogate the allowlist cache. This is not a public Postfix interface, and Postfix’s developer never intended that people should poke at it. I have no problem telling people “this isn’t meant for you, and it might change in the future, and you shouldn’t rely on any of the other data it reveals, but here’s how you glimpse at it.” But that still leaves me figuring out how to grovel through the stupid cache. Turns out you have to specify the cache format on the command line, a hint which appears nowhere in the documentation because you’re not supposed to go poking at the cache.
Anyway.
That’s a day. Forty words written, and I still don’t know why Postfix didn’t immediately try the backup MX.
The fiction crashed to a halt this month, because of aforementioned family crunch. That’ll restart next month. I owe the world an orc baseball story. I’ve figured out how to make that a short story, finally. One of the rules to making a story short is to limit the number of characters, but a baseball team has nine players, so I’d just like to say oops this was a terrible idea.
Ah well. Live and learn. Learn something that will do you absolutely no good in the future, because part of you already knew it.
I’ve taken sponsorships on the mail book, but I’m pondering doing a Kickstarter for it anyway. Sponsors and Patronizers will get theirs, of course, but there’s a broad pool of folks who want a thing to be ready to produce before they buy it. I’m also pondering stretch goals like “for $25k, I will put the book contents on a public web site.” I’d still have the book in stores, of course. But the ebook won’t be available on Kindle. Heck, the way this book is going the ebook might be $19.99. It’s gonna be freaking huge. Anyway, that Kickstarter and such stretch goals is just idle fancy. Some authors have good results with making their books public. For others, it destroys sales.
Which am I?
Only one way to find out, and the test costs only a year’s work.
That’s it for this month. Thanks for Patronizing me. Onward!