Amazon recently introduced Author Rank, where they list authors in order of popularity. I’ve had a lot of discussions about this feature and what it means to writers.
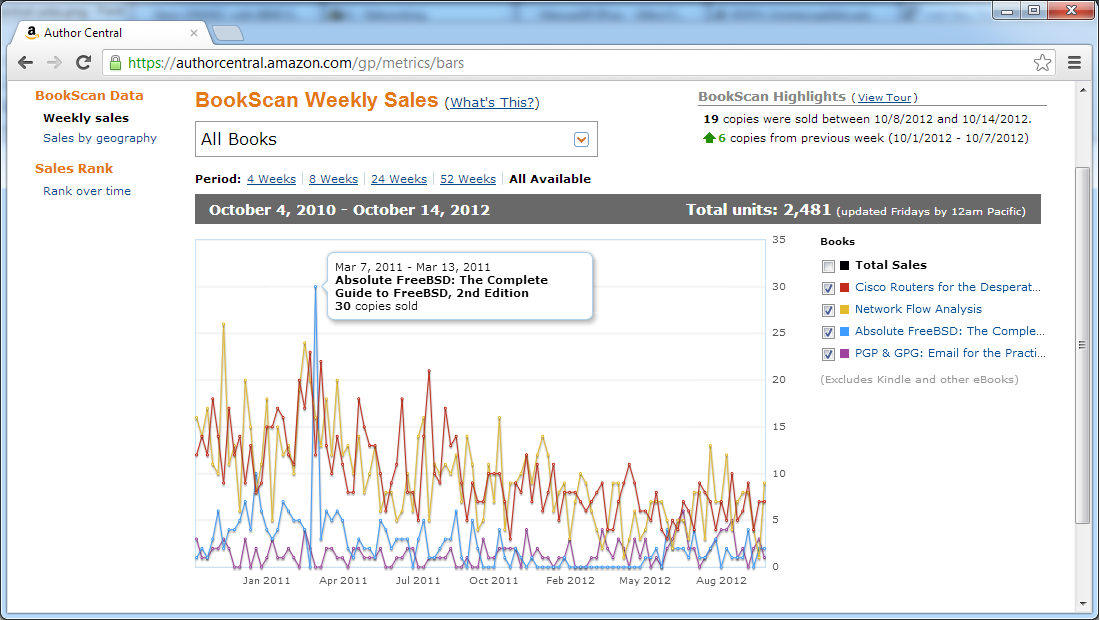
Amazon provides a surprising number of features for authors. Their Author Central system lets me see how many of which book sold, and where, over a given time period. There’s a neat little app that shows where in the country my books sold, according to Bookscan data. Bookscan data might not be complete, but it’s more information than my twice yearly No Starch royalty statements. I know that in the last four weeks, five of my NSP books sold in the SF-Oakland-San Jose area, and 4 in Washington, DC. That’s interesting, and for a tech author those sales numbers are not too shabby.
I choose the word “interesting” carefully. It’s interesting. But it’s not exactly useful. If these geographic sales charts show that I was consistently selling quite well in Amarillo, Texas, I might be inclined to see what’s going on down there. But the sales basically hit exactly where I expect: Silicon Valley, Washington DC, RTP, NYC, with others trailing.
An author can spend hours trawling through his sales data this way. It’s interesting, but: this data doesn’t help you sell books. It makes sense that you’d kill a couple hours the first time you get the data, but as an ongoing thing, it just takes up time. You’d be better off writing.
Author Central also gives graphs of how your books as a whole, or all your books, sell over time.
Looking at this, I might think “Wow. What did I do the week of March 7, 2011? Why did that book do so well that week? And how can I repeat this?” The answer is, I didn’t do anything. This sales spike had nothing to do with me. I wrote a good book. Someone ordered a bunch of copies, perhaps for a test, perhaps for their company, or perhaps because the paper the book is printed on is thin and soft. All I can do is be appreciative of “the folks who bought my book,” whoever they are.
The more insidious question would be: “why have my sales dropped since then?” I have an easy answer. My print sales have dropped, but my ebook sales have increased. Also, technology books have a lifespan. I’m pleasantly stunned that the five-year-old Absolute FreeBSD is still selling this well, but I have no right to expect this trend to continue.
It’s conceivable that I might find a use for this data. If my books consistently sell well in Amarillo, a place not known for its high tech business, I’d probably want to investigate and see what’s happening down there. Perhaps I would somehow use Amarillo in a new book, to give a nod to that readership. But the data fits my expectations, so it won’t change anything I do.
Also, this graph contains data. X number of book Y sold in Week Z. Those are real numbers. Not terribly useful, but interesting.
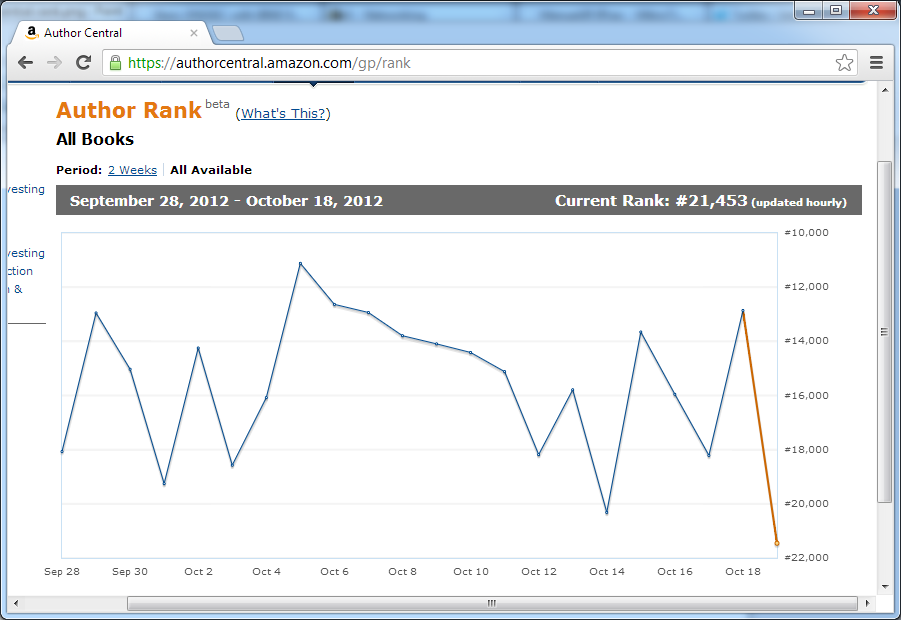
Now consider the Amazon Author Rank graph.
On October 5th, I was the #11,117th most popular author on Amazon. Think about that for a moment.
What is popularity? How is it calculated? What is that supposed to mean? Is that an average based on the sales of all of my books, or my sales in aggregate? How are authors ranked? Without this kind of knowledge, this chart isn’t data. It’s an arbitrary rank, no better than Klout. I’d actually find my Scalzi Number more useful; I know how that’s calculated, and hence could derive a shallow meaning from it.
This number will cause an author some kind of emotional reaction. Maybe they’re disappointed that 11,116 authors are more popular than them. Maybe they’re thrilled that hundreds of thousands of authors are less popular than them. Either way, this reaction does not help an author with their craft.
Ranking authors by some unknown popularity algorithm? It’s like high school all over again, and just as meaningful.
When this feature just came out, I exchanged tweets with other authors about it. Chris Sanders, author of Practical Packet Analysis, shared with the world that his author rank was 9425, a few thousand higher than mine.
I agree that his Practical Packet Analysis is a good book. But what am I to draw from him having a higher Amazon rank than I do?
I write the books I write. My Network Flow Analysis is the best book I can create on netflow. PPA is the best book Chris could write about Wireshark. Comparing them isn’t really possible: they’re different topics, different audiences, and completely different books. Even though both are books about networking, they are utterly different in purpose, execution, and readership.
And what does the difference mean? Does his one book sell more copies than all of my books compared together sell less than his? Could be. Even if his books outsell mine twenty-five to one, does it matter to me?
One of the very worst things an author can do is start comparing himself to other authors. That way lies despair and heartbreak. If I measured my success against Dean Koontz or James Patterson, or even Richard Stevens, I’d give up writing altogether. Because my books aren’t their books, my audience isn’t their audience, and my career is not their career. I write the best books I can. And my audience finds them useful enough to buy them. That’s enough.
You want to be a more popular author? Write the best books you can. Continuously work to improve your craft. Become a better author, and readers will come. Don’t get involved in high-school popularity contests, especially ones that offer no benefit to your career, your craft, or your ego.
Personally, I’m going to ignore Author Rank. I see no use for it. The best thing you can do is shut up and write.
And lest someone gets the wrong idea, I like Chris. If I get to Charleston, I plan to look him up and see if he’s free for lunch. I’m sure he knows where to get good barbeque. Mind you, he can pay for it. He’s the big-name popular author, after all.
Hey, maybe Author Rank isn’t completely useless…